
IT Network Support for San Diego Manufacturers, Uptime, Security, Proof
Summary: IT network support is the steady work that keeps your plant connected, secure, and ready for audits. IT includes segmentation, patching, monitoring, backup testing, and clear proof you can show to a customer or an auditor.
By Peter Noble, Founder of Noble Technology Group

IT network support that respects the plant clock, with restore tests you can show.
What IT network support means, a simple definition
IT network support is the steady work that keeps your plant connected, secure, and ready for audits. IT covers switches, firewalls, Wi-Fi, Servers, and the Cloud. IT ties identity to access. IT keeps logs and backups in order. IT also includes clear notes that prove what was done. Think of IT as the base that lets your shop run jobs on time. IT is the foundation for managed network services and for business network support. IT is the day to day work that makes problems small and progress clear.
Why IT network support matters to uptime and delivery
Your machines, your ERP, and your people depend on the network. If IT is slow, your crew waits. If IT drops, the floor goes quiet. Uptime is your promise to your customers. IT network support helps you keep that promise.
Wi-Fi, printing, and DNC queues
When Wi-Fi is weak, travelers do not print. When a driver or a programmer cannot pull down a file, a cell sits idle. DNC queues back up. A simple survey and smart placement fix many of these issues. We review channel use and signal strength. We move or add access points. We set clear SSIDs for shop devices and for guests. We make it simple for workers to connect, and we keep traffic safe and separate. That is small business network support done with care.
ERP and QMS availability
Your ERP and QMS tie the plant together. They need a clean lane. We make sure your switches and firewalls are set to give those systems priority. We test print to label devices. We test scan to server and scan to email. We watch for small delays. We fix them before a line manager notices. This is network monitoring and management that respects your schedule.
IT network support for compliance and audits
Many San Diego shops face flow down requirements. You may hear about NIST SP 800 171, CMMC Level 2, ITAR, or ISO and AS frameworks. These are not just words. They affect contracts and insurance. They also affect how you run your day. Auditors want to see proof that you control access, keep backups, patch systems, and handle incidents with clear steps. IT network support creates that proof.
Mapping support work to NIST SP 800 171 and CMMC Level 2
We take plain tasks and map them to control families. Access control, we remove shared logins and use groups by role. Audit and accountability, we keep logs and we keep them safe. Configuration management, we document changes and keep device backups off the device. Identification and authentication, we enable multi factor that your team can accept. Incident response, we write a short plan and practice it. Maintenance, we set an after hours window and we keep a record. System and information integrity, we patch on a schedule and we verify results. You do not need long speeches. You need a plan that you can follow and a binder you can show.
Evidence binder, access reviews, restore tests
Auditors believe what they can see. We keep an evidence binder that is current and simple. It includes screenshots of settings, export files for access lists, change logs, restore test notes, and short incident summaries. We run quarterly access reviews and remove accounts that do not belong. We test restores each month and record time to recover and success checks. That is how IT compliance services turn claims into proof.
Managed network services, what steady work looks like
Network inventory and current state
We start with a walk. We map switches, firewalls, access points, controllers, servers, and core apps. We note versions and support status. We listen to what slows your day. We draw a one page diagram that shows the current path for your traffic. You see what you have and where it goes. This is the base for every smart step that follows.
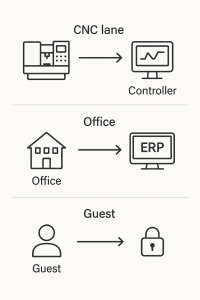
Simple lanes reduce noise and risk, and they make audits easier.
Segmentation for CNC, DNC, and office systems
Flat networks create noise and risk. We place machines and controllers on their own lane. We keep ERP, file shares, and office work in another lane. Guests belong in a safe lane of their own. We write clear rules. We test with your team. We keep the names simple so anyone can understand. This is VLAN segmentation for CNC and DNC done with care.
Wi-Fi survey and tuning for the shop floor
We check signal levels, client counts, and channel use. We adjust channels to reduce overlap. We balance power levels. We add access points where needed. We set SSIDs that reflect roles. Shop devices connect to a stable SSID with proper rules. Guests get easy access that stays away from business traffic. We test with handhelds and laptops while a shift runs. This is a shop floor Wi-Fi survey in simple steps.
After hours patching plan
No one wants a surprise reboot at two in the afternoon. We make a plan. We set a window after the last truck leaves. We patch servers, switches, firewalls, and access points during that window. We test before and after. We keep notes. We send a short log you can read in one minute. That is IT support and services aligned to production, not the other way around.
Identity, roles, and multi-factor
Shared logins create risk and fail audits. We move to named accounts. We tie access to groups that match roles. We enable multi-factor with a simple push prompt. We review admin access each quarter. We log changes to groups and remove access when people change roles. We link the review to your evidence binder so you can show an auditor that you manage access with care.
Monitoring and alerting that respect the crew
We watch the network, but we do not flood your team with alerts. We tune thresholds. We act first, then we inform. We keep a ticket open until we have a cause and a fix. We close the loop with a short summary. This is network monitoring and management designed for busy leaders who need answers, not alarms.
Vendor coordination, clear outcomes
When the carrier blames the firewall and the ERP vendor blames the network, you lose time. We take the lead. We gather facts. We join the call. We use packet captures and simple tests to show what is real. We keep a timeline. We own the outcome. We send a summary in plain words. This is how a trusted advisor behaves.
Real client stories, proof without hype
A medical provider that needed steady help and clear words
A local animal hospital had urgent work and tight schedules. They needed remote sessions that worked and projects that moved without drama. We set a rhythm for regular care. We answered calls. We explained in simple terms. They called us reliable and flexible, and they said we were the whole package.
A marine services office that wanted less noise and faster answers
This team had bounced between providers. Tickets dragged. Notes were unclear. We simplified the process. We answered the phone. We fixed issues and wrote clear notes for every step. They said their office ran smooth. They said our team was friendly and respectful to all employees.
A company with sites from the Atlantic to Hawaii
Time zones can turn small problems into big ones. We adjusted our schedule. We met them where they were. We solved issues in real time across locations. They said this wide coverage was a major benefit and that we were there for them.
Ready to see steady results?
Schedule a free 20 minute consult at a time that works for you. We will review your network, share a one page plan, and answer your questions in plain words.
The first 90 day plan, simple and repeatable
Days 1 to 10, listen and map
We walk the floor. We meet leads from production, quality, and admin. We gather configs and notes. We record software versions and support dates. We point out quick wins that add value now. We flag higher risk items for planned work. We prepare a one page summary with next steps, owners, and times.
Days 11 to 30, stabilize and protect
We take the quick wins. We set safe defaults on the firewall. We define VLANs and rules and test them off hours. We move shared logins to named accounts. We start backup verification and run the first restore test. We begin a weekly status note with simple bullets and clear owners.
Days 31 to 60, document and prove
We finalize the network diagram. We set change windows and write them down. We run a one hour tabletop drill for incident response. We collect evidence for access reviews, patch logs, and restore tests. We clean the ticket board and close what is complete. We deliver an evidence binder that is current and clear.
Days 61 to 90, optimize and plan
We tune Wi Fi with live data. We check ports for errors and clean up old trunks. We confirm logging and alert thresholds. We build your one year roadmap with budget ranges. We agree on a quarterly review rhythm. You end the quarter with less noise, fewer surprises, and a plan that fits the work you do.
Change control and maintenance windows, a checklist that works

Clear steps reduce risk and keep nights calm.
Before the window
- List the change in simple words
- Note the device, the backup location, and the roll back plan
- Name the people on call
- Define success checks that matter to the floor
During the window
- Take a device backup
- Make one change at a time
- Run the success checks
- Record the result with times
After the window
- Share a short note with what changed and what passed
- Update the diagram or the rule sheet if needed
- File the log in the binder
Sample change log entry
Date, device, action, backup saved to share, rule added to allow DNC to file server, tests passed, program sent to a machine, traveler printed, ERP login worked, result, success, owner, Peter, next step, monitor for errors for twenty four hours.
Restore testing with examples, what good looks like
File level test
Pick a known folder with CAD and CAM files. Delete a test copy, then restore it. Record start time and end time. Verify that the files open. Save a screenshot of the restore job and the folder view.
Database test
Pick a test database from ERP or QMS. Restore to a test server. Record time to mount and test a known report. Take screenshots of the steps. Note success criteria, report opens, data looks right, no errors in logs.
Image level test
Restore a server image to a sandbox. Boot it. Check services. Confirm that core apps start. Record times. Save screenshots. Note that this is not a production restore. It is a proof step that shows you can recover if you must.

A backup is a promise, a restore is the proof.
RTO and RPO in plain words
Recovery time objective is how long you can wait before work must resume. Recovery point objective is how much data you can lose and still be okay. We set these with you. We test to see if the plan meets them. We write down the results. This helps with audits and with cyber insurance. It also helps you sleep.
Compliance mapping in plain words
- Access control, use named accounts, use groups by role, review access each quarter, remove old accounts fast
- Audit and accountability, keep logs from key systems, store them where they are safe, review after changes and incidents
- Configuration management, keep a device inventory, keep backups off the device, log changes with date, time, person, and reason
- Identification and authentication, enable multi-factor for remote and admin access, set strong but usable password rules
- Incident response, write a short plan, practice it, keep a call tree, record what happened and what you learned
- Maintenance, patch after hours, test before and after, keep a log, share the results
- Risk assessment, list your top five risks each quarter, set fair impact and chance, fix the best return items first
- System and information integrity, use endpoint protection you can see and manage, keep it current, respond with clear steps
Common network gaps and fixes
Old switches with no support
We plan a refresh. We choose gear that fits the work, not a spec sheet. We schedule the cutover after hours. We test with a checklist. We label ports in clear words. We keep old configs for safety.
Flat networks that mix machines and office work
We design segments. Machines get their space. Office work gets its space. Guests get their own space. We write rules that let traffic flow where it should. We block what should not pass. We test with the floor team.
Shared logins and weak identity
We move to named accounts. We set groups for roles. We add multi-factor that is easy to use. We keep a clean list of admin accounts. We remove access fast when people leave or change roles.
Backups that no one has tested
We schedule a monthly restore test. We time it. We check success. We record proof. We talk about what we learned. We adjust. Over time, you feel calm because you have seen it work.
Wi-Fi that drops or lags on the floor
We tune channels and power. We add access points where needed. We set clear SSIDs and rules. We test in motion with the devices your crew uses. We watch for roaming problems. We fix them.
Local knowledge, why the San Diego context matters
San Diego plants serve aerospace, defense, and medical device firms. Flow downs are common. Audits are frequent. Your buildings vary. Some are older with thick walls and odd cable runs. Summer heat changes how gear behaves. Traffic on local freeways affects how fast help can arrive if you need on site support. We plan around these real world factors. We pick change windows that respect late rush jobs in National City. We plan Wi-Fi for tall racks in Kearny Mesa. We consider line of sight issues in Otay Mesa. We show up in La Mesa and El Cajon. Local matters. IT changes how we design and how we schedule.
Training that people accept
- Ten minute stand up on phishing signs
- Five minute demo on secure file transfer for a vendor
- Quick review on why we patch at night
- Friendly reminder on badge and door habits
We keep the tone respectful. We honor the time. We link each point to uptime and safety. When people feel respected, they follow the plan.
Incident Response without panic
Bad days can happen. A user clicks a bad link. A switch loops. A service fails. The difference is how we respond. We have a plan. We have a call tree. We have first steps for each role. We contain the issue. We recover. We learn. We write a short summary. We share what we will change so it does not happen again. This is network security support in action. Calm, clear, and helpful.
What to ask any provider before you decide
- Can you show a recent restore test with start and end times
- Can you show a change log from an after hours patch window
- How do you schedule work around first article runs and changeovers
- Will I have named owners for network and for security
- How will you document VLANs and firewall rules so my team can follow
- How do you handle calls with carriers and software vendors
- Will you map your work to my compliance framework and give me an evidence binder
- How will you show progress each month in one page
The Noble Technology Group approach and what you can expect
We begin with your schedule. We ask what must not break. We ask when you can accept change. We align our windows to your flow. We bring a plan, a checklist, and a fallback plan. We do the work. We test. We show proof with screenshots and short notes. We leave the site better than we found it. We follow up the next day.
As your trusted advisor, we connect managed IT services, IT support and services, and IT compliance services. That means we see the full picture. If a network change touches a server, we own both. If a policy change affects a floor device, we plan the rollout with you. If an auditor asks for a sample, we provide it. You do not have to herd vendors. You focus on production, we focus on results.
Calls to action
FAQ, quick answers for busy plant leaders
What is the difference between it network support and managed network services
It network support is the core work that keeps devices, links, and settings in good shape. Managed network services include that work plus a wrap of help desk, reporting, vendor management, and planning. Both matter. Together they give you steady days and clear nights.
How does it network support help with CMMC Level 2 in a machine shop
It turns requirements into tasks you can show. Named accounts, groups for roles, multi-factor, device backups, change logs, restore tests, and short incident notes. We map each task to control areas. We keep an evidence binder. When an auditor asks, you open the binder and share proof.
When should a plant segment CNC and office traffic
Segment now if machines and office share the same lane. It will reduce noise and risk. It will also make incident work easier. We design simple lanes with names your team will understand. We test with a real job before we cut over.
What proof should I bring to a cyber insurance renewal
Bring a summary of your stack, EDR, MFA, backup with immutability, and logging. Bring the last three restore tests with times. Bring a short policy set for access, change control, and incident response. Bring a note on how you train staff.
How often should we run a restore test and what should it include
Run one each quarter. Rotate file, database, and image tests. Record start and end times. Verify that the data opens and that services start. Keep screenshots. Note who ran the test and what they learned.
What does an after hours patch window look like
It starts with a list of changes and a backup. It moves step by step with tests after each change. It ends with a short note that shows what changed and what passed. If something fails, roll back and try again another day.
Summary and next steps
It network support is not a mystery. It is steady work that keeps your shop connected, secure, and audit ready. It uses simple steps and clear proof. It respects your plant clock. It cuts noise and builds trust. IT gives you better days on the floor and calmer nights for your leaders.
You deserve a partner who shows up, listens, plans, and proves. Noble Technology Group offers managed IT services, IT support and services, and IT compliance services in San Diego. We design work around your runs. We back every change with a plan and a test. We keep your evidence clean. We answer the phone. We own the outcome.



