
A secure island for CUI keeps production moving and evidence clean
NIST 800-171r2 Compliance for Manufacturers, A Practical Guide by Noble Technology Group
Quick Answer, A Manufacturer’s Eight Step Path to 800 171r2
- Identify CUI and map flows across email, CAD, CAM, ERP, file servers, and cloud storage.
- Define a boundary so CUI lives in a smallest secure island, then build simple bridges to the rest of the business.
- Choose the right Microsoft 365 and Azure approach for your contracts, then enforce identity, device, and data controls.
- Harden endpoints and servers with encryption, patching, and allow listing where practical, measured with clear reports.
- Protect data in transit and at rest, reduce risky email attachments, and control removable media with check in and check out discipline.
- Centralize logs and evidence, retain enough history to answer who, what, and when, and satisfy auditor requests.
- Train your people by role, run short tabletop drills, and make security a normal habit on the floor and in the office.
- Write a living SSP and POA&M, score honestly, submit to the right portals, and run a quarterly cadence that never stops.
Why 800-171 r2 Matters To Manufacturers Right Now
Manufacturing teams once treated security as a cost of doing business. Today it is a competitive advantage. Your primes want suppliers who can show discipline, who understand CUI, and who can prove they have a real program. The standard asks you to protect confidentiality through one hundred and ten requirements across fourteen families. For the authoritative reference, see https://csrc.nist.gov/pubs/sp/800/171/r2/upd1/final and the assessment companion, https://doi.org/10.6028/NIST.SP.800-171A.
In practice, 800 171r2 shifts three things on day one. First, data classification becomes real. You decide what is CUI, you label it, and you control where it goes. Second, your scope and boundary become explicit. You define which systems are in and which are out, then you defend that line with technology and procedure. Third, documentation and evidence become part of daily work. Your System Security Plan explains what you do, your POA&M explains how you close gaps, and your evidence proves the program is real.
Story One, Coastal Marine Repair Gets Incident Ready
A coastal marine repair firm handled drawings and work packages with sensitive markings. The gap was clear. The team did not have a proven path to file a cyber incident report if something went wrong, and leadership worried that the requirement would create confusion when time mattered most.
We wrote a concise incident response plan, procured the certificate needed to access the reporting portal, assigned a primary and a backup, tested access on two separate workstations, and practiced a short scenario. A phishing email lands, a user reports, the lead validates, logs are pulled, and a decision is made. The drill focused on chain of command, communication, and evidence capture. The change in confidence was immediate.
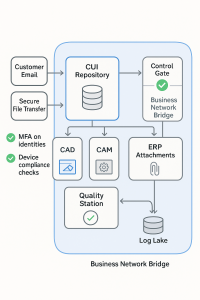
Keep CUI inside a small secure island, connect to the rest of the business with a controlled bridge
How Manufacturers Define a CUI Boundary And Build An Enclave
The most reliable path is to build a small, secure island where CUI lives, then connect that island to your broader business with controlled bridges.
- Scope your island. Place CAD and CAM systems, the document control repository, sensitive email mailboxes, and any cloud storage that holds drawings or work instructions inside the island. Keep general accounting, HR, and CRM outside. Document the decision in your SSP.
- Control identity. Every person has one identity with strong multi-factor authentication. Access to CUI folders and mailboxes is granted by role and reviewed monthly.
- Control devices. Only compliant, encrypted, and patched devices can reach the island. Shared floor devices use individual logins, short timeouts, and session locks that match production realities.
- Build simple bridges. Replace email attachments with links to controlled repositories. Use secure transfer for large files and keep automatic logs.
- Make change control boring. Put a gate in front of software installs, driver updates, and configuration changes. Simple requests, quick approvals, and clean logs.
SSP, POA&M, And SPRS, What Auditors Expect And How To Prepare
Your SSP explains how each requirement is satisfied in your environment. Your POA&M lists every gap with a target date and owner. Your score is calculated honestly and submitted through the proper channel. For self assessment structure, manufacturers often consult https://doi.org/10.6028/NIST.HB.162.
- Tell the truth, no boilerplate that does not match your reality.
- Point to living evidence, tickets, logs, training records, screenshots, and approvals.
- Assign names, each control has a clear owner.
- Update on a cadence, quarterly refresh keeps details accurate and your team ready.
Microsoft Options, Commercial, GCC, Or GCC High For 800 171r2
The right choice depends on contract language, data categories, and collaboration needs. Align tenant capabilities with sensitivity and configure identity, device, and data controls to match the standard. For control mappings, see https://learn.microsoft.com/en-us/azure/governance/policy/samples/nist-sp-800-171-r2.
A precision machine shop adopted a secure island anchored by a Microsoft tenant. Conditional access allowed only compliant devices into sensitive repositories, role based access governed folders, and logs flowed to a central workspace. Programmers moved away from thumb drives because the approved path was faster and more reliable.
Protect Data In Transit And At Rest Without Slowing Work
- Encrypt at rest in cloud and on premises repositories.
- Encrypt in transit for email and file transfer.
- Replace email chains of attachments with links to controlled storage.
- Use a secure transfer workflow for oversized files, with automatic logging.
- If physical media is required, label it, log it, and record destruction.
Centralize Logs And Evidence, See What Matters And Prove It
Centralize logs from identity, endpoints, servers, and cloud platforms. Retain them long enough to tell a complete story. Build simple dashboards that show failed sign-ins, device compliance, patch status, and access to sensitive repositories. During an incident, your team can pull a timeline in minutes. During an assessment, your team can show exactly how you meet requirements.
Train Your People By Role, Keep It Short And Useful
Machinists handle printed travelers and removable media. Inspectors manage measurement data tied to sensitive jobs. Buyers receive supplier messages with sensitive drawings. Office staff handle contracts and email. Keep training short, focused, and regular. Use the language of your shop. Add two tabletop exercises a year for the incident response team.
Story Two, Precision Machining Builds A Secure Island That Speeds Work
We mapped how sensitive files enter, move, and leave. We built a secure island with clear edges and one bridge to the business side for purchasing and finance. We enforced device compliance before access and provided a fast path for programmers to move models into the correct repository. The result was speed and clarity, fewer thumb drives, faster starts, and visible compliance metrics.
Five Pitfalls That Derail Manufacturers And How To Avoid Them
- Confusing FCI and CUI. Teach recognition, label clearly, and use controlled repositories.
- Letting email become a filing cabinet. Move sensitive attachments into repositories and send links.
- Leaving shared local admin rights. Use requests for temporary elevation and record the change.
- Skipping evidence capture. Logs, tickets, and screenshots prove the control is real.
- Treating compliance as an IT project only. Operations owns the process, IT enables and proves.
Supplier Flowdown For CUI, Simple Controls That Protect Your Chain
Protect the chain with clear purchase order clauses, secure transfer methods, and acknowledgment records kept with the job file. When a prime asks for proof, you have it ready. When a supplier has a question, you have a simple answer.
Evidence Pack, What Auditors Ask To See Most Often
- Identity and access reviews with manager sign off
- MFA enforcement reports, including exception approvals where needed
- Device compliance snapshots, encryption and patch status by group
- Change control samples for recent updates and installs
- Training records and summaries of tabletop exercises
- Incident log entries with timelines and outcomes
- Supplier acknowledgments and secure transfer logs by job
The Ninety Day Plan That Fits A Shop Schedule
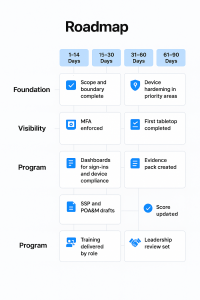
Three focused lanes deliver visible progress without slowing production
Days one through fifteen
Conduct a focused gap assessment, confirm scope, write the boundary, draft the SSP, and calculate your current score.
Days sixteen through forty five
Enforce multi-factor authentication, tighten administrative access, and harden devices that touch sensitive work with maintenance windows that match your shifts.
Days forty six through seventy five
Stand up controlled repositories, move sensitive attachments out of email, roll out role based access, and train machinists, inspectors, buyers, and office staff.
Days seventy six through ninety
Centralize logging, run your first tabletop exercise, finalize top tier policies, create your first evidence pack, and update your score and SSP.
Story Three, From Reactive Projects To A Program Mindset
We replaced scramble and fix with a quarterly cadence that includes risk review, policy refresh, control checks, tabletop drills, evidence sampling, supplier acknowledgments, and a concise leadership briefing. Fewer surprises and faster closings followed. The team stopped dreading assessments and started welcoming them.
Managed IT Services That Move You Faster
Predictable cost mapped to control coverage, reliable outcomes from standard images and policies, and speed when it matters. Your partner arrives with context, evidence, and a plan. They know your people and your environment and can act without a learning curve.
IT Support And Services On The Floor And In The Office
Controls must fit the work. A five axis control PC cannot lock every minute, and a CMM station cannot reboot mid measurement. Policies should allow practical exceptions with compensating safeguards. Patch windows align with maintenance. Admin changes are requested in a simple form and approved quickly. Every exception is written and justified.
IT Compliance Services That Tie It All Together
Compliance is a management system. A strong program brings structure, artifacts, and cadence. With the right setup you turn 800-171 r2 from a source of stress into a source of confidence.
Story Four, A Phish Meets A Prepared Team
A buyer reported a suspicious message, the lead validated, logs confirmed no session token, a password reset followed, and the incident record captured the timeline. Because the mailbox could contain sensitive messages, the team ran a threshold check. No external report required, evidence attached, training reinforced, all within half an hour.
A Straightforward Budget Conversation
Start with scope and boundary. Price work in three tracks, foundation, visibility, and program. Add project based items only when needed. Cap your monthly number and demand reports that show coverage by control family. Ask providers for redacted samples of an SSP, an evidence pack, and a monthly report.
Frequently Asked Questions
Is NIST 800-171 r2 still relevant with a newer revision in view
Yes. Many contracts continue to reference revision two today. Close revision two gaps while staying aware of future changes. For the current text, see https://csrc.nist.gov/pubs/sp/800/171/r2/upd1/final.
Do small manufacturers need GCC High to protect sensitive information
It depends on contract clauses and data types. Some can meet obligations in Commercial or GCC with proper controls, others require GCC High. Align the choice to sensitivity and collaboration needs, and review control mappings such as https://learn.microsoft.com/en-us/azure/governance/policy/samples/nist-sp-800-171-r2.
How do we calculate and submit an SPRS score
Review each requirement, document your implementation in the SSP, log gaps in your POA and M, calculate your score, and submit through the correct portal. For self assessment structure, see https://doi.org/10.6028/NIST.HB.162.
What is required for DFARS 252.204-7012 incident reporting
You must recognize, contain, document, and report qualifying incidents in a timely manner. Name a primary and backup, test access to the portal, and maintain logs that support follow up questions.
What counts as CUI in a machine shop
Examples include drawings with sensitive markings, work instructions tied to defense programs, certain measurement files, and contract deliverables that meet defined categories. Consult the https://www.archives.gov/cui and your customer.
Why Manufacturers Choose Noble Technology Group
We specialize in manufacturers across San Diego and National City. We understand how work really happens, in programming, on the floor, in quality, in purchasing, and in leadership reviews. Our managed IT services stabilize your environment. Our IT support and services keep your people moving. Our IT compliance services build the structure and cadence that makes 800-171 r2 manageable. We speak plainly, we move quickly, and we stand with you during assessments and incidents.
Calls To Action
Schedule a readiness call. If you want a clear view of your posture, your SSP, or your score, schedule a twenty minute readiness call. We will review your top risks and outline a ninety day plan. Visit our website or call 619 752 1620.
Request a boundary and enclave workshop. If you are deciding between uplifting the whole network or building a secure island, our half day design workshop will give you a diagram and a costed path that leadership can approve.
Ask for a sample evidence pack. We will share a redacted packet with training records, logging summaries, and change control samples that pass real reviews.
Enroll your team in role based training. Short modules for machinists, inspectors, buyers, and office staff create habits that protect sensitive information without slowing work.




