Security Awareness Training That Actually Changes Behavior
I am Peter Noble, founder of Noble Technology Group in La Mesa. I spend my days shoulder to shoulder with owners, general managers, compliance leaders, and front line teams across San Diego County. We keep machines running, protect sensitive data, and help people win audits without drama. Over the years I have learned something simple and stubborn, technology does not stop social engineering, people do. Security awareness training is the difference between clicking and pausing, between a near miss and an incident report, between a culture that holds the line and one that apologizes later.
This is my straight talk guide to security awareness training that works in the real world. You will see how we blend managed IT services, responsive IT support and services, and practical IT compliance services into a steady, repeatable training program that fits your business, your people, and your production schedule. You will also hear the voices of real clients who have trusted us over the years, because proof matters more than promises.
https://nobletechgroup.com/initial-consultation/
What Security Awareness Training Really Means For San Diego Manufacturers
Security awareness training is not a slide deck once a year. It is a rhythm. It is short, clear, specific moments that move people from passive to alert. It is stories, quick practice, and simple rules. It is phishing simulations that feel like the messages your team actually receives. It is five minute videos that someone on the shop floor can watch between changeovers. It is a huddle where a supervisor holds up two suspicious emails from the morning and asks, what would you do, then confirms the right steps. It is a culture that says, we ask before we click, we slow down when money moves, we verify voice requests with a second channel.
In our work across San Diego manufacturing, healthcare, and service businesses, we see the same reality. Your attackers do not need rare vulnerabilities. They need a busy person, a believable invoice, and a bit of urgency. Training works when it speaks to that reality. Training fails when it expects people to memorize every acronym and exception. The goal is not perfect knowledge. The goal is consistent behavior.
Why Training Matters For Owners And GMs
If you lead a company, your risks sit in three buckets. Revenue risk from production stoppage and lost time, regulatory risk from violations and penalties, and reputational risk from a breach that often shows up on a Friday afternoon. Security awareness training touches all three. It reduces click through on malicious emails, it reinforces the policy controls you put in place for audits, and it creates a common language so anyone can raise a hand when something feels off. Owners do not need more dashboards. Owners need to know that people know what to do.
I have seen the relief on a manager’s face when a near miss stays a near miss because a coordinator paused, asked, and verified before approving a bank change request. That moment does not happen by accident. It happens because leaders model it and because we practice it.
The Threats Employees See Every Week
Forget the headline breaches and the jargon. These are the common patterns your team faces.
- Phishing and business email compromise, an email that looks like a vendor, a client, or a leader, asking for credentials, invoices, gift cards, or bank changes.
- MFA fatigue prompts, rapid fire approval notifications that train people to click approve without thinking.
- QR code scams, a printed code on a break room flyer or a code in a PDF that drives to a credential page.
- Fake vendor portals, a familiar looking invoice portal that steals logins.
- Cloud sharing requests, a shared file from an unknown account that says view now, urgent.
- Tailgating and help desk pretexting, a friendly voice or a casual walk in that relies on kindness and speed.
- USB baiting and personal device crossover, curiosity and convenience that collide with policy.
What It Looks Like When Training Works
Let me ground this in real client experience and outcomes. We have supported companies through fires, audits, and the daily grind of tickets and changes. One of our longest standing manufacturing clients summed up what they expect from us and why they stay.
When our company headquarters burned down, we feared the worst. All our systems, managing multiple locations, were housed in that one building. Thanks to Noble Technology Group, we were back up and running the very next day. This level of reliability and trust is why we turned to NTG in the first place. Their expertise in implementing IT plans, especially during challenging transitions like moving to Office 365, has been invaluable. They consistently handle both foreseeable and unforeseeable issues with quick, effective responses. What also sets NTG apart is their deep understanding of CMMC and cybersecurity for government requirements. They are proactive, and they maintain real relationships. — Elliot LeGros, Westflex, inc.
That story is disaster recovery, not a phishing simulation. So why share it in a training guide, because culture shows up everywhere. The same steady, no drama posture that brings a plant back online the next day is the posture we bring to training. Prepare, rehearse, execute, report back. Do the work, do not make a scene.
I was locked out of my computer for a while. I called Lisa who had this thing up and running within seconds of answering the phone. It is good to know that Noble has me covered. — Dante Hunt, Google review
That is more than a compliment. It tells you why training adoption sticks. People trust the process when support shows up fast, when the help desk is human, when the fix is straightforward. Security awareness training lives or dies on that same trust. If people feel talked down to, they will tune out. If they feel respected and supported, they will lean in.
Noble Technology Group assisted me with an urgent compliance challenge and supported my team throughout the process of becoming certified. Thanks Peter and the amazing team. — Mark Harmsen, Google review
Compliance is full of controls about access, change management, incident response, and awareness. A documented training program with sign in, content, role fit, and evidence logs ties directly into those requirements. Awareness is not a checkbox. It is a control that shows up across the framework.
Our Security Awareness Training Program, Managed IT Services, IT Support, And IT Compliance Working As One
How Noble Technology Group aligns security awareness training with CMMC Level 2 and NIST SP 800-171 requirements for audit readiness.
We build training like we run operations. Simple, local, accountable, and evidence backed. Here is our framework.
Baseline assessment and quick wins
We start by sampling your current risk surface. We review recent incidents and near misses, we pull a small set of simulated phishing emails, and we look at your policy set. We ask, what is the top friction your people face each week. Then we deliver quick wins, a short message from leadership about invoice verification, a sign at the shipping desk about badge checks, a refresher on how to report suspicious email.
Role based learning paths
Executives handle wire fraud and public messaging. Supervisors handle access and approvals. Front office staff handle invoices and vendor changes. Shop floor teams handle badge access and removable media risk. Healthcare teams handle protected health information. We tailor by role so people hear what matters. For regulated scopes, we align content to controls so your evidence binder stays audit ready and supports cyber insurance requirements.
Micro learning and repetition
We schedule training in small units. Five to ten minutes, not fifty. We place learning where work happens. A micro lesson before a financial approval window. A simulation during a known busy time, with instant feedback. A weekly tip in a team channel. A one page visual on the procurement board that says stop, call, confirm.
Phishing simulations that feel real
We craft simulations that mirror your vendor base, your tone, your common file types, and the way your customers talk. We do not shame people. We help them spot patterns. After each wave, we hold a short review for the team and a private coaching for anyone who clicked. The point is growth, not blame.
Incident walk throughs and tabletop exercises
We run short exercises that include who speaks to customers, who issues a password reset, who makes the call on system isolation, and who logs the event. We keep these practical and short. If you are in scope for CMMC Level two or NIST SP 800 171, we capture each session as evidence with sign in, agenda, and outcomes so your auditor can see that you practice, not just plan.
Metrics the front office actually uses
We track click rate, report rate, time to report, and completion rate by role. We highlight trend lines. If your report rate climbs and your click rate drops, your culture is moving the right way. If an area lags, we target a refresher.
Integration with managed IT services, IT support and services, and IT compliance services
Training is part of our managed IT services. It works best when your support desk, your change windows, your patch cadence, your backup testing, and your incident response speak the same language. When our help desk closes a ticket with a quick win, when our compliance team updates a policy, when our network team adjusts segmentation, training reinforces that move.
Evidence, proof, and audit readiness
Every training session creates an artifact. Date, roster, topic, and materials. We store and index it so when you need to prove awareness controls, you can do it in minutes. If you are preparing for a CMMC assessment or a customer security questionnaire, we align the artifacts with your policy set and your system security plan.
https://nobletechgroup.com/initial-consultation/
Three Common Training Missteps And How To Avoid Them
You start with a tool, not a plan
Simulations matter, but they are not a plan. Buy a tool without a rhythm and you will get reports that no one reads. Start with people, roles, busy seasons, and your top three risks.
You outsource culture
You can hire us to build the program, but leadership sets the tone. When your team sees you pause to verify a payment request, that lesson sticks.
You confuse compliance with security
Compliance matters. We help clients pass audits and maintain evidence. A certificate does not stop a click. Train to reduce real risk, then map results to your controls.
A Practical Cadence That Fits San Diego Workflows
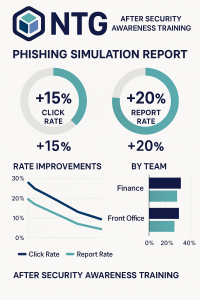
Real-world metrics from Noble Technology Group’s security awareness training program, proving measurable improvement in employee response.
Week one
Kickoff with leadership, set goals, pick the top risks to focus on, run a small baseline phishing test, publish a two minute video on reporting suspicious emails, and confirm your reporting channel.
Week two
Run a finance focused micro drill on vendor bank change verification, send a three minute reminder to supervisors on badge checks and visitor protocols, and follow up one to one with anyone who clicked in week one.
Week three
Run a voice pretext simulation to the front desk and a short role play for supervisors, then share a short story internally about a recent near miss that someone caught.
Week four
Close the loop with a five minute update on click and report rates, celebrate wins, note one improvement area, and schedule the next wave.
While that cadence runs, our team continues routine work, patching, backup checks, endpoint hardening, and ticket response. The training amplifies adoption, the support reinforces training, the compliance documentation maintains audit readiness. It is one system, not a set of disconnected parts.
Security Awareness Training FAQ
What is security awareness training
Security awareness training is a steady program that helps employees recognize and respond to threats like phishing, business email compromise, and social engineering. The goal is consistent behavior, not perfect knowledge.
How often should security awareness training run
We recommend a monthly rhythm with micro lessons and periodic simulations. Short sessions fit production schedules and create stronger habits than occasional long sessions.
Does security awareness training help with CMMC Level two audits
Yes. Training artifacts, rosters, and tabletop notes support awareness and incident response controls in CMMC and NIST SP 800 171. Clean evidence saves time during audits.
What metrics prove security awareness training works
Click rate, report rate, time to report, and completion by role. Upward report rate and downward click rate show a culture that is learning and responding.
Final Word And Clear Next Step
Security awareness training should feel like part of the way you already work. Short, steady, real. It should help people do their jobs without slowing production. It should prove value in fewer clicks and faster reports, not just in a binder. If you want a partner who will run the whole system, from managed IT services to IT support and services to IT compliance services, and do it with the steady tone you see in these client stories, we would be honored to help.
https://nobletechgroup.com/initial-consultation/
Prefer to talk now, call 619-752-1620 and ask for Peter. We will listen first and give you a straight answer.



