 The New Linux “Plague” Backdoor: What It Means For Your Business—and How We Stay Ahead At Noble Technology Group
The New Linux “Plague” Backdoor: What It Means For Your Business—and How We Stay Ahead At Noble Technology Group
By Peter Noble, Founder & CEO, Noble Technology Group
If you run a business in San Diego and your operations depend on Linux servers—file shares, line‑of‑business apps, databases, or cloud workloads—this matters. Security researchers just spotlighted a stealthy Linux threat, a PAM-based backdoor nicknamed Plague, that’s been hiding in plain sight for months by quietly bypassing authentication and slipping through standard security controls. As someone who spends my days keeping clients compliant, insured, and operational, I want you to understand what’s happening, why it’s so slippery, and how we build a layered defense so a problem like this doesn’t become tomorrow’s outage—or worse, a data breach that jeopardizes contracts and insurance coverage.
“This isn’t a smash‑and‑grab. It’s a patient intruder who steals a key, blends in, and uses your front door.”
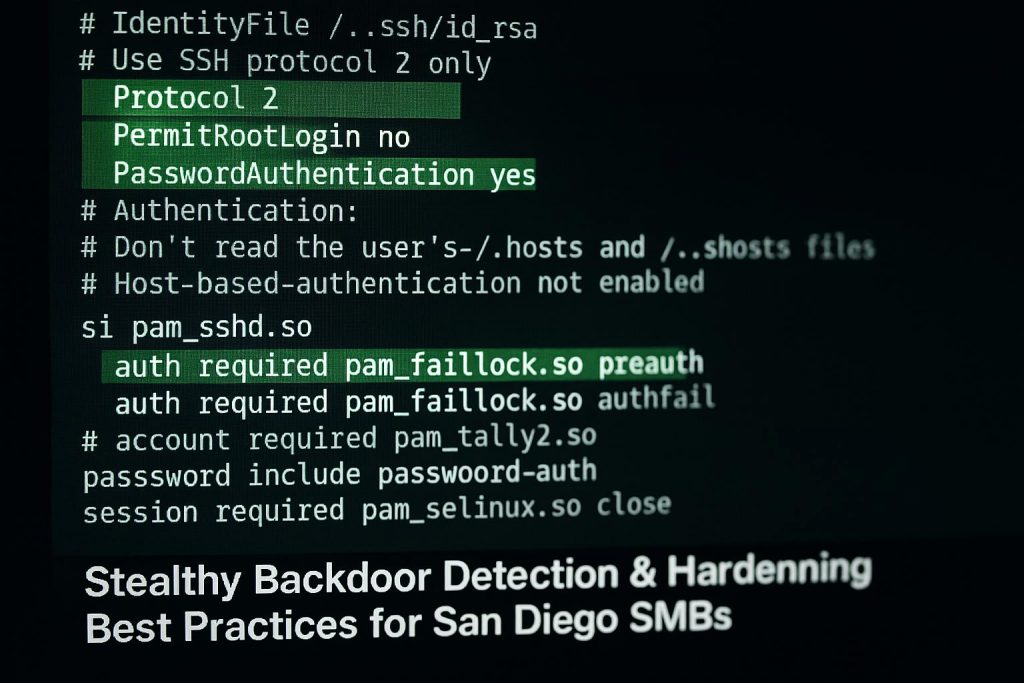
What Is “Plague” And Why It’s Different
Linux uses Pluggable Authentication Modules (PAM) to decide who gets in and how. Plague disguises itself as a legitimate PAM module, hooks directly into that process, and bypasses normal authentication, granting attackers persistent, covert SSH access—often without tripping basic alarms. Think of it as swapping one bouncer’s badge with another. On paper it looks real; in practice it’s an impostor with full privileges.
Multiple undetected samples uploaded to VirusTotal over an extended period suggest active development and effective evasion. That’s why this class of backdoor can quietly persist across updates and go unnoticed in environments relying only on signature‑based tools.
How Plague Stays Hidden
- Static credentials baked in for covert access.
- Obfuscation and anti-debugging, making reverse engineering harder.
- Environment tampering—for example, unsetting SSH variables and redirecting shell history to
/dev/null. - Deep integration with PAM so it survives system updates and blends with legitimate authentication flows.
“If your detection strategy begins and ends with ‘Is there a known signature?’, you’ll miss the attacks designed to leave none.”
“We’re Not A Big Target”—Why Small And Mid‑Size Teams Still Need To Care
Smaller organizations often have lean IT teams and limited monitoring on Linux compared to Windows. Meanwhile, Linux quietly runs the critical stuff—databases, ERP, production scheduling, web apps, email gateways, and self‑hosted tools. That’s a bullseye for attackers who prefer durable beachheads over noisy smash‑and‑grab campaigns.
In regulated and supply‑chain‑sensitive spaces—manufacturing (CMMC), healthcare (HIPAA), finance (GLBA/PCI), legal, defense industrial base—an undetected backdoor can escalate quickly from “IT incident” to compliance failure, contractual breach, and cyber insurance claim denial if minimum controls weren’t in place.
Signs You May Have A Problem (Even If Nothing Looks “Wrong”)
- Odd SSH logins or unexpected geographies.
- Minor PAM edits or suspicious look‑alike libraries (e.g.,
libselinux.so.8) in unusual paths. - Gaps in logs or inconsistent shell histories; missing or redirected
HISTFILE. - Service restarts tied to PAM/sshd without a legitimate change.
“Logs don’t lie, but good backdoors make them forget.”
The Business Risk In Plain English
- Lateral movement into Windows or cloud identities.
- Data exfiltration (CAD, PHI, financials, contracts).
- Payload deployment like miners or ransomware.
- Abuse of your infrastructure to attack partners and customers.
Our Playbook: How We Keep Clients Ahead Of Evasive Linux Threats
1) Lock Down Authentication—Make The Front Door Boring
- Enforce MFA for SSH via centralized identity or hardware tokens.
- Disable direct root SSH; require
sudowith per‑user accounts. - Limit SSH exposure: bastion hosts or VPN with short‑lived certs.
2) Treat PAM And SSH As Tier‑0 Components
- File integrity monitoring on PAM configs and critical libraries.
- Signed updates and golden baselines for rapid diffing.
- Configuration drift control via IaC or enforced templates.
3) Watch Behavior, Not Just Signatures
- EDR for Linux around
sshd, PAM, and shells. - Detect environment tampering and anomalous histories.
- Continuous log analytics with correlation for geo/time anomalies.
4) Reduce Blast Radius
- Least privilege and short‑lived admin elevation.
- Network segmentation between production, management, and backups.
- Immutable backups with separate credentials and recovery tests.
5) Prove It—So Auditors And Insurers Believe It
Turn controls into artifacts—tickets, baselines, training logs, and detection reports—so you can demonstrate maturity for CMMC, HIPAA, PCI, and cyber insurance underwriting.
What Cyber Insurance Is Really Asking For
- MFA everywhere (VPN, email, privileged access, remote admin).
- EDR/XDR on servers and endpoints, including Linux.
- Centralized logging with 90+ days hot retention.
- Vulnerability management with SLAs and exceptions tracked.
- Privileged access management for admin credentials.
- Immutable backups and tested restores.
- Security awareness training with measurable completion.
- Incident response plan with roles and evidence steps.
Real‑World Proof From Clients
“Since switching to NTG, our systems have become streamlined, with minimal downtime to billing, emailing, and customer communication… their deep understanding of CMMC and cybersecurity… big enough to deliver top‑notch service, yet small enough to maintain real relationships.” — Cole Dick, General Manager, Pacific Crest Services
“When our company’s headquarters burned down… Thanks to Noble Technology Group, we were back up and running the very next day… They consistently handle both foreseeable and unforeseeable issues with quick, effective responses.” — Westflex (case story)
“Peter and Roody… are always available… They know their stuff and always get us taken care of!” — Sarah Gonzalez (Google review)
“The whole Noble Tech team is friendly and very respectful to all our employees… They will continue to be our IT Support Team.” — Susan Martinez, California Marine Cleaning, Inc.
A Practical Linux Security Checklist You Can Use Today
Authentication & Access
- MFA for SSH; disable password logins; rotate keys; expire stale accounts; restrict by IP/bastion.
PAM & Config Integrity
- Monitor
/etc/pam.d/*; verify signatures; alert on new shared objects; tie changes to tickets.
Logging & Telemetry
- Centralize logs; detect env tampering and history suppression; maintain 90–180 days searchable.
System Hardening
- Patch kernels/OpenSSH; reduce packages/ports; enforce SELinux/AppArmor; integrity checks; isolate workloads.
Backup & Recovery
- Immutable backups with separate credentials; quarterly restore tests; defined RTO/RPO.
Human Layer
- Linux‑specific admin training; peer review of sensitive scripts; tabletop exercises.
How We’d Handle A Suspected Plague Case—Step By Step
- Stabilize & Contain: isolate the host, snapshot data.
- Preserve Evidence: volatile captures; secure configs and logs.
- Rapid Triage: diff against baselines; hunt telltales; check outbound beacons.
- Eradicate & Recover: replace components; rotate secrets; rebuild if needed.
- Close The Loop: document, update policies, produce artifacts for auditor/insurer.
“Detection matters. Evidence matters more.”
Your 30‑60‑90 Day Plan (If You’re Running Linux In Production)
Next 30 Days
- MFA on SSH; disable passwords; baseline PAM; centralize logs with rules for SSH anomalies.
Days 31–60
- Segment networks; rotate keys; require
sudo; run tabletop exercises; strengthen change control.
Days 61–90
- Immutable backups + restore tests; close Linux vuln backlog; compile an “evidence binder.”
Let’s Make This Simple
With the right managed IT services, IT support, IT consulting, and compliance services, you can lower risk, improve resilience, and keep insurance and auditors happy—without slowing the business.
See more on https://www.nobletechgroup.com/ and https://www.nobletechgroup.com/our-clients/ page. When you’re ready, Schedule a Consultation.


